Read on if you are interested in the following topics:
- Why the CISO Should Not Report to the CIO
- Why You Should Assume you Have Been Hacked
- 6 Kill Chain Fundamentals You Must Know
- 7 ‘Must Ask and Prove’ Questions a CIO/CISO must ask about their Next Gen Firewall
- How Can You Deny Command and Control Attacks
- Cybersecurity Canon Books – Hall of fame for Cyber Security Books – Readers are leaders
- Scaling Security with Real Cooperation between companies happening now
- AI’s (Artificial Intelligence’s) Role in Info Sec.
- The Beginnings of AI and Security
- Alan Turing Should be a Hero!
- Learn how Alan Turing cut WW2 by 2 years and saved 20 million lives
Rick and I had a fantastic and varied discussion about the above topics. He not only reports directly to the CEO (rare) but he has serious technical chops as well. He is an avid reader whose interests include various security sub topics. He has some great suggestions on books, movies, etc.
Links to all resources mentioned and actionable steps are all listed below. If you prefer to listen to the entire episode use appropriate links below.
Highlights and Things to Learn and Research
- Evolution of the CISO role (It is barely a 10-20 year old profession still)
- The CISO should not report to the CIO. Why?
- Who should the CISO report to?
- Who owns risk in the Enterprise?
- Why Alfred Sloan’s approach will not work for the CISO now. Not only do we discuss Rick’s opinion on this subject but here is a link to a powerpoint presentation “The evolution of the Cybersecurity Trifecta CIO/CSO/CISO” he did on this topic at RSA 2015. The evergreen value of this presentation will last for many years so it is well worth seeing.
- You must believe that Threat Protection is still possible. The 1st goal must be to prevention (95%). The remaining (5%) can be focused on detection and remediation, but don’t let vendors dominate the 5%. Be great at the 95%. Rick and I both share this message.
Understanding 6 Steps of the Kill Chain
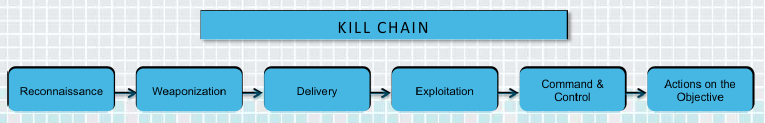
The adversary has not been successful until the last step has been performed.
The Lockhead Martin original paper on this topic is titled: Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains Eric Hutchins, et al
Assume that you have been hacked
Courage: Have the courage to assume you have been hacked and develop your tactics from this assumption. One of the first things that you will employ and deploy is that you will decide to be great at Network Security Monitoring. Now you might outsource this function but that is ok. With the assumption that there is a major shift in tactics.
Rick advocates reading Richard Bejtlich’s book below The Practice of Network Security Monitoring.
Listen to Rick talk about the specific areas related to network monitoring that Bejtlich advocates @16:45 of the interview.
By purchasing point products for each point in the kill chain, you pay for monitoring three times! No one except big government agencies can afford this because you need to:
- Pay for it
- Maintain it
- Read and understand the data
Next Gen Firewalls can support you in the kill chain. These are the specific areas that you need to ask about. Don’t get lost in the details and confusion. Follow these steps all highlighted in the original kill chain paper above.
Next Generation Firewalls: 7 ‘Must Ask and Prove’ Questions a for a CIO/CISO to ask
Does your Next Gen Firewall participate in the Kill Chain? Where?
- Authenticated users – Can you map to them?
- Are all documents flowing into the network being examined?
- Are you mapping users to applications? – Applications can be blocked as needed
- Are files being delivered into the network inspected to ensure non-malicious behavior?
- Is an IPS inline inspection in place to look for recon activity?
- Command and control – do you have URL filtering and Passive DNS filtering?
- End Point Protections – Are the services tied together? Vendors have placed this on the customer and should be assisted at the vendor level
Author’s Note
- Segment you network at a firewall level. I call this an intrawall.
- Make sure you understand the true power of your Next Gen Firewall. Are the services turned off or on? What modules do you own? Are you current with maintenance?
- Get rid of your layer ¾ firewall.
- Make sure that you have not turned your great Next Gen Firewall into a Layer ¾ firewall.
Cybersecurity Canon Project – Hall of Fame for Cybersecurity Books
To identify a list of must-read books for all cybersecurity practitioners — be they from industry, government or academia — where the content is timeless, genuinely represents an aspect of the community that is true and precise, reflects the highest quality and, if not read, will leave a hole in the cybersecurity professional’s education that will make the practitioner incomplete.
Rick Howard, Palo Alto Networks Chief Security Officer, proposes the Cybersecurity Canon: a list of must-read books where the content is timeless, genuinely represents an aspect of the community that is true and precise, and, if not read, leaves a hole in a cybersecurity professional’s education that will make the practitioner incomplete.
To see the complete list of books from 2014 and 2015 and also see Rick’s presentation on the topic visit this link.
2015 Winners
- We Are Anonymous: Inside the Hacker World of LulzSec, Anonymous, and the Global Cyber Insurgency By Parmy Olson
- Cuckoo’s Egg
- Winning as a CISO
- Spam Nation
- Countdown to Zero Day
Threat Intelligence and Information Sharing
Rick’s Favorite Books
- Cryptonomicon by Neal Stephenson
“The best hacker novel of all time” – Rick Howard
Rick’s Top Movies
- War Games – with Matthew Broderick
- Hackers – with Angelina Jolie
- The Matrix – with Keanu Reeves
- The Imitation Game – with Benedict Cumberbatch
Rick’s Hero Alan Turing

- Imitation Game – semi-true biography of the work Turing did at Bletchley Park during WWII
- Turing Played by Benedict Cumberbatch
- Proved mathematically that it is possible to build a computer years before we had the technology to build it
- Proved mathematically you can put a set of symbols into a machine to make it do one thing today, and the next day, input a second set of symbols to get it to do something else
- Helped build the machine that would break the German Enigma Encryption Machine that generated German codes during WWII
- It is estimated he reduced WWII by 2-4 years
- Developed an AI test to determine if a computer is ‘intelligent’ – Turing test
- Put a person behind a screen in front of a terminal. That person then asks a question.
- The person must decide if the answer he hears is given by a human or a computer. If the person thinks a human gave the answer when it was in fact a computer, then that computer is ‘intelligent’
 Billboard Question: If you could put up a billboard in every major city, what would you want the message to be?
Billboard Question: If you could put up a billboard in every major city, what would you want the message to be?
Security Billboard:
You should be worried about threat prevention. It is not only possible, but you should absolutely be doing it
Personal Billboard:
1) The security community is filled with people with different personalities, colors, thoughts, political beliefs, etc. so be tolerant of the person down the hall from you no matter how crazy he is.
2) Bring women into the security conversation, otherwise half the brains on the planet are being excluded
Rick’s Bio

Rick Howard is the CSO for Palo Alto Networks where he is responsible for the company’s internal security program, the oversight of the Palo Alto Networks Threat Intelligence Team, and the development of thought leadership for the cyber security community. His prior jobs include the CISO for TASC., the GM of iDefense and the SOC Director at Counterpane. He served in the US Army for 23 years., and spent the last 2 years of his career running the Army’s CERT. Howard holds a Master of Computer science degree from the Naval Postgraduate School and an engineering degree from the US Military Academy. He taught computer science at the Military Academy and contributed as an executive editor to two books: “Cyber Fraud: Tactics, Techniques, and Procedures” and “Cyber Security Essentials”
Rick can be found here
To Contact Bill: email him at billm@redzonetech.net
Love this episode? Leave a Review
Share it on your LinkedIn feed.
If you haven’t already, please make sure you leave us a review on iTunes.
About Bill Murphy
Bill Murphy is a world-renowned IT Security Expert dedicated to your success as an IT business leader.
Connect With Us On Social Media
Connect with Bill on LinkedIn.
Instagram
Twitter
Facebook
Join The CIO Innovation Mastermind Community
We invite the top 20% of Business IT Leaders for my CIO Innovation Mastermind Events group to participate in monthly discussions on things like VR, AI, and other disruptive & emerging technologies. If you want to become a member, email Chief of Staff, Jamie Luber Jluber@redzonetech.net for more information.





